AWS Solutions Architect/training/Section 5: Advanced Amazon VPC
- 42. Introduction
- 43. The AWS Global Infrastructure - connected by high-speed backbone network between the regions.
- Made of 26+ regions. Each region has two or more Availability Zones - for redundancy. An availability zone can be thought of as a physical data center. Each data center has redundant power sources and redundant networking.
- AWS Outposts - extends AWS services into dedicated hardware in your data center or corporate location. For using AWS services on-premises. For using AWS APIs on-premises.
- AWS Local Zone - exxtends the AWS Availability Zone closer to end-users for lower latency. I guess it's like an Availability Zone without the full-fledged characteristics of a Data Center?
- AWS Wavelength Zone - extends AWS using 5G wireless. For singled-digit ms latency to mobile device users.
- AWS CloudFront is a CDN with 13+ Regional Edge Caches and 400+ Edge locations.
- 44. Defining VPC CIDR Blocks
- 8 host bits = 256 addresses /24 subnet mask 255.255.255.0
- 16 host bits = 65,536 addresses /16 subnet mask 255.255.0.0
- 12 host bits = 4096 addresses /20 subnet mask [1]
- Cannot increase or decrease the size of your CIDR block once it's defined (You'd have to create and migrate to a new VPC)
- Recommended to use RFC 1918 ranges [2]
- https://docs.aws.amazon.com/vpc/latest/userguide/subnet-sizing.html
- Solarwinds has an interactive (not obvious) calculator https://www.solarwinds.com/free-tools/advanced-subnet-calculator and there's a similar calculator at https://www.site24x7.com/tools/ipv4-subnetcalculator.html
- 45. [HOL] Create a Custom VPC
- Sometimes when using the AWS console, they will give you the equivalent AWS CLI commands to execute the same action. e.g.
aws ec2 attach-internet-gateway --vpc-id "vpc-0a00177c33db94123" --internet-gateway-id "igw-0daed3800abd56791" --region us-east-1
- Sometimes when using the AWS console, they will give you the equivalent AWS CLI commands to execute the same action. e.g.
- 46. VPC Routing Deep Dive
- Routing between "local" cloud resources and an identical local (private) IP address connected via VPG to on-premises data center
- Routing when you want all return traffic from the Internet to pass through a security appliance
- 47. Security Groups and Network ACLs
- Security Groups can be applied to instances in any subnet
- SG has an implicit DENY
- Network ACLs are at the network level (subnet)
- Network ACLs are numbered, and processed in order, so an explicit DENY would be ignored (not reached) if an earlier ALLOW permitted the traffic.
- 48. [HOL] Configure Security Groups and NACLs
- 49. NAT Gateways and NAT Instances
- A NAT Gateway would be created in a public subnet, and be used to allow outbound traffic from instances on a private subnet (e.g. to download software and patches).
- The route for the NAT Gateway needs to be in the private subnet.
- A NAT Gateway is a managed service whereas a NAT Instance is your self-deployed instance. The managed is automatically scalable and offers some other advantages, but you'll pay for the privilege. A NAT instance can double as a bastion host (or "jump host" for SSH), but since you're managing it, you'll need to do the extra work for "features".
- AWS example at https://docs.aws.amazon.com/vpc/latest/userguide/vpc-example-private-subnets-nat.html
- 50. [HOL] Private Subnet with NAT Gateway
- 51. Using IPv6 in a VPC
- AWS assigns a /56 IPv6 address range to your VPC
- Subnets receive a /64 address range allowing 18 million trillion addresses.
- A hexadecimal pair (00 - FF) is assigned for each subnet, providing for 256/64 subnets e.g. 2406:da1c:f7b:ae00::/56
- You can have an "Egress-only" Internet Gateway to allow IPv6 traffic outbound but not inbound.
- 52. [HOL] Configure IPv6
- test with
ping6orping -6
- test with
- 53. VPC Peering
- enables routing using private IPv4 or IPv6 addresses.
- CIDR blocks cannot overlap - which is another argument against using IPv4 for anything
- Is not transitive, so each VPC must establish peering to every other VPC that you want to route to. IOW, you need to setup and manage the entire mesh of networking.
- 54. [HOL] Configure VPC Peering
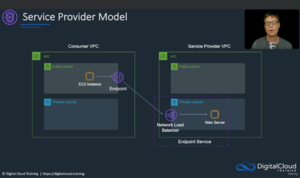
- 55. VPC Endpoints
VPC Endpoints[3] offer a highly secure and efficient method for connecting your AWS resources to specific AWS services, ensuring that your data remains within the AWS network, and minimizing exposure to the public internet. There are two types:
- VPC Interface Endpoints create an Elastic Network Interface (ENI) in the private subnet of your EC2 instance, connecting to public services like AWS API Gateway, AWS CloudFormation, AWS CodeDeploy and AWS CloudWatch.
- As VPC interface endpoints utilize AWS PrivateLink, you'll be charged for those endpoints by the hour and by the introduced data transfer.
- IAM policies can be applied to endpoints. So, Security can be provided by Security Groups
- Bucket policies can limit access to endpoint source.
- VPC Gateway Endpoint uses a route table entry to provide private network access to "public" AWS services with no added costs. However, only AWS S3 or AWS DynamoDB are supported.
- Security is provided by VPC Endpoint Policies.
- VPC Interface Endpoints create an Elastic Network Interface (ENI) in the private subnet of your EC2 instance, connecting to public services like AWS API Gateway, AWS CloudFormation, AWS CodeDeploy and AWS CloudWatch.
- 56. [HOL] Create VPC Endpoint
References
- ↑ https://en.wikipedia.org/wiki/Classless_Inter-Domain_Routing#IPv4_CIDR_blocks
- ↑ The Internet Assigned Numbers Authority (IANA) has reserved the following three blocks of the IP address space for private internets:
10.0.0.0 - 10.255.255.255 (10/8 prefix) 172.16.0.0 - 172.31.255.255 (172.16/12 prefix) 192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
We will refer to the first block as "24-bit block", the second as "20-bit block", and to the third as "16-bit" block. Note that (in pre-CIDR notation) the first block is nothing but a single class A network number, while the second block is a set of 16 contiguous class B network numbers, and third block is a set of 256 contiguous class C network numbers.
- ↑ AWS Fundamentals Blog