Certbot: Difference between revisions
(add keytool example) |
(link to README) |
||
| (15 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
{{Feature | |||
|image=Electronic Frontier Foundation video conferencing background certbot-logo-1 (28343180089).png | |||
|imgdesc=Certbot | |||
}} | |||
{{#set:feature title = {{PAGENAME}} }} | |||
{{#set:feature description = Certbot, from the Let's Encrypt project of the EFF, provides free and automated SSL certificates. }} | |||
{{#set:feature notes = For non-public sites, we can still generate certificates using DNS }} | |||
{{#set:feature tests = [https://www.ssllabs.com/ssltest/analyze.html?d={{SERVERNAME}} Test on SSL Labs.com] }} | |||
{{#set:feature examples = See [[:File:Certificate grade.png]] }} | |||
Certbot is a tool that allows you to manage the Transport Layer Security ([[TLS]]) of your Webserver. | Certbot is a tool that allows you to manage the Transport Layer Security ([[TLS]]) of your Webserver. | ||
{{ambox| | |||
|type = content | |||
|text = | |||
I recently added Certbot automation to the freephile Meza fork ([https://github.com/freephile/meza/blob/qb/src/roles/ansible-role-certbot-meza/README.md README]), so you can have automatic TLS certificates with your [[MediaWiki]] platform. | |||
[[User:Admin|freephile]] ([[User talk:Admin|talk]]) 17:05, 16 December 2024 (EST) | |||
<br /> | |||
}} | |||
== Let's Encrypt == | == Let's Encrypt == | ||
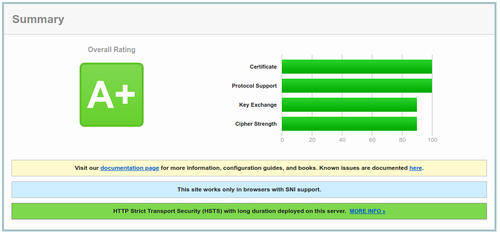
We used to run certificates from StartSSL because they offer free one-year certificates. However, today we upgraded to using 'LetsEncrypt' and our certificates are both more secure and easier to manage. Instead of a "B" grade, we now have "A" grade security. <ref>https://www.ssllabs.com/ssltest/analyze.html</ref> | We used to run certificates from StartSSL because they offer free one-year certificates. However, today we upgraded to using 'LetsEncrypt' and our certificates are both more secure and easier to manage. Instead of a "B" grade, we now have "A" grade security. <ref>https://www.ssllabs.com/ssltest/analyze.html</ref> | ||
[[File: | [[File:Certificate grade.png|left|500px]] | ||
'''Certbot''' ([https://github.com/certbot/certbot code]) is a fully-featured, extensible client for the Let's Encrypt CA (or any other CA that speaks the ACME protocol) that can automate the tasks of obtaining certificates and configuring web servers to use them. This client runs on Unix-based operating systems. It '''requires''' root access | '''Certbot''' ([https://github.com/certbot/certbot code]) is a fully-featured, extensible client for the Let's Encrypt CA (or any other CA that speaks the ACME protocol) that can automate the tasks of obtaining certificates and configuring web servers to use them. This client runs on Unix-based operating systems. It '''requires''' root access to manage yourself - but is built-in to many service providers today as it has become an industry standard. | ||
Until May 2016, Certbot was named simply <code>letsencrypt</code> or <code>letsencrypt-auto</code>, depending on install method. Instructions on the Internet, and some pieces of the software, may still refer to this older name. | Until May 2016, Certbot was named simply <code>letsencrypt</code> or <code>letsencrypt-auto</code>, depending on install method. Instructions on the Internet, and some pieces of the software, may still refer to this older name. | ||
| Line 11: | Line 30: | ||
[https://certbot.eff.org/#pip-apache Certbot website] at EFF.org (the Electronic Frontier Foundation). | [https://certbot.eff.org/#pip-apache Certbot website] at EFF.org (the Electronic Frontier Foundation). | ||
== | == Automation == | ||
Ansible has a [https://docs.ansible.com/ansible/latest/collections/community/crypto/acme_certificate_module.html ACME certificate module] in the '''crypto'''' collection (community not core). However, using it is a two-step process. We opted instead to create an integration into the Meza platform that takes care of both installation and renewal. | |||
== With HAProxy == | == With HAProxy == | ||
| Line 20: | Line 40: | ||
Like [https://www.lighttpd.net/ Lighttpd], [http://www.apsis.ch/pound/ Pound], [https://www.ejabberd.im/ Ejabberd] and other servers, [[Load balancer|HAProxy]] expects a single <code>.pem</code> file that has the combined contents of the <code>fullchain.pem</code> and <code>privkey.pem</code>. | Like [https://www.lighttpd.net/ Lighttpd], [http://www.apsis.ch/pound/ Pound], [https://www.ejabberd.im/ Ejabberd] and other servers, [[Load balancer|HAProxy]] expects a single <code>.pem</code> file that has the combined contents of the <code>fullchain.pem</code> and <code>privkey.pem</code>. | ||
Fortunately, certbot offers a --pre-hook, a --post-hook and a --renew-hook that we can use. | Fortunately, certbot offers a --pre-hook, a --post-hook and a --renew-hook that we can use. The hooks allow to stop and later restart the 'normal' services and also concatenate the generated certificate files into a .pem file for HAProxy. | ||
Do not use the [https://github.com/greenhost/certbot-haproxy plugin]. | |||
== On Amazon == | == On Amazon == | ||
| Line 38: | Line 58: | ||
The best way for Cloudflare customers to encrypt '''fully''', is to use Certbot. Cloudflare support echoes [https://support.cloudflare.com/hc/en-us/articles/214820528-How-to-Validate-a-Let-s-Encrypt-Certificate-on-a-Site-Already-Active-on-Cloudflare word-for-word] what Let's Encrypt says in their community forum: [https://community.letsencrypt.org/t/how-to-get-a-lets-encrypt-certificate-while-using-cloudflare/6338 How to get a Let's Encrypt certificate while using CloudFlare] | The best way for Cloudflare customers to encrypt '''fully''', is to use Certbot. Cloudflare support echoes [https://support.cloudflare.com/hc/en-us/articles/214820528-How-to-Validate-a-Let-s-Encrypt-Certificate-on-a-Site-Already-Active-on-Cloudflare word-for-word] what Let's Encrypt says in their community forum: [https://community.letsencrypt.org/t/how-to-get-a-lets-encrypt-certificate-while-using-cloudflare/6338 How to get a Let's Encrypt certificate while using CloudFlare] | ||
tldr; Use the <code>--webroot-path </code> option with the <code>certonly | tldr; Use the <code>--webroot-path </code> option with the <code>certonly --preferred-challenges="dns"</code>, but you'll need to manually intervene. Optionally, if you just turn off the proxying while you issue the certificate, you can use TLS-SNI and HTTP-01 challenges (and then turn proxying back on.) For more advanced usage, check out the docs where they describe [https://certbot.eff.org/docs/using.html#pre-and-post-validation-hooks pre and post validation hooks] | ||
With the pre-hook and post-hook options, you can script the conditions needed to authenticate and renew. | With the pre-hook and post-hook options, you can script the conditions needed to authenticate and renew. | ||
<code>certbot renew --pre-hook "service nginx stop" --post-hook "service nginx start"</code> | <code>certbot renew --pre-hook "service nginx stop" --post-hook "service nginx start"</code> | ||
The <code>--renew-hook</code> only runs when a certificate has been successfully renewed, so use this script to do things like concatenate the fullchain and | The <code>--renew-hook</code> only runs when a certificate has been successfully renewed, so use this script to do things like concatenate the fullchain and | ||
== Resources == | == Resources == | ||
| Line 56: | Line 76: | ||
== FAQ == | == FAQ == | ||
; How do I obtain a new certificate?: | ; How do I obtain a new certificate?: | ||
:<ol><li>setup the SSL virtual host in Apache, and be sure to include some <code>SSLCertificateFile</code> and <code>SSLCertificateKeyFile</code> directives using the "snake-oil" certs.<br /> e.g. <br /> SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem <br /> SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key<br /><li>Then run certbot<br />/opt/certbot/certbot | :<ol><li>setup the SSL virtual host in Apache, and be sure to include some <code>SSLCertificateFile</code> and <code>SSLCertificateKeyFile</code> directives using the "snake-oil" certs.<br /> e.g. <br /> SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem <br /> SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key<br /><li>Then run certbot<br />/opt/certbot/certbot --apache -d example.org,www.example.org,wiki.example.org --dry-run<br />/opt/certbot/certbot --apache -d example.org,www.example.org,wiki.example.org</ol> | ||
; What certs do I have?: | ; What certs do I have?: | ||
: sudo | : sudo certbot certificates | ||
; How do I see more info about my certificates? | ; How do I see more info about my certificates? | ||
| Line 67: | Line 87: | ||
: <source lang="bash">sudo keytool -printcert -sslserver equality-tech.com</source> | : <source lang="bash">sudo keytool -printcert -sslserver equality-tech.com</source> | ||
; How do I expand a cert to include some sub-domains? | ; How do I expand a cert to include some sub-domains? | ||
: sudo /opt/certbot/certbot | : Use the <code>--expand</code> option to put multiple domains in the same cert. | ||
: sudo /opt/certbot/certbot certonly --cert-name example.org --expand -d example.org,www.example.org,wiki.example.org,example.com,www.example.com,wiki.example.com | |||
; How do I create a wildcard certificate with LetsEncrypt? | |||
: See https://github.com/geerlingguy/ansible-role-certbot/pull/60#issuecomment-423919284 | |||
; How do I cleanup my old/test certificates?: | ; How do I cleanup my old/test certificates?: | ||
: sudo /opt/certbot/certbot | : sudo /opt/certbot/certbot revoke --cert-path /etc/letsencrypt/live/baz.example.org/cert.pem | ||
: sudo /opt/certbot/certbot | : sudo /opt/certbot/certbot delete --cert-name baz.example.org | ||
{{References}} | {{References}} | ||
Latest revision as of 05:53, 17 December 2024
| Certbot | |
|---|---|
 | |
| Image shows: | Certbot |
| Summary | |
| Title: | Certbot |
| Description: | Certbot, from the Let's Encrypt project of the EFF, provides free and automated SSL certificates. |
| More | |
| Notes: | For non-public sites, we can still generate certificates using DNS |
| Test: | Test on SSL Labs.com |
| Example: | See File:Certificate grade.png |
Certbot is a tool that allows you to manage the Transport Layer Security (TLS) of your Webserver.
| I recently added Certbot automation to the freephile Meza fork (README), so you can have automatic TLS certificates with your MediaWiki platform.
freephile (talk) 17:05, 16 December 2024 (EST) |
Let's Encrypt[edit | edit source]
We used to run certificates from StartSSL because they offer free one-year certificates. However, today we upgraded to using 'LetsEncrypt' and our certificates are both more secure and easier to manage. Instead of a "B" grade, we now have "A" grade security. [1]
Certbot (code) is a fully-featured, extensible client for the Let's Encrypt CA (or any other CA that speaks the ACME protocol) that can automate the tasks of obtaining certificates and configuring web servers to use them. This client runs on Unix-based operating systems. It requires root access to manage yourself - but is built-in to many service providers today as it has become an industry standard.
Until May 2016, Certbot was named simply letsencrypt or letsencrypt-auto, depending on install method. Instructions on the Internet, and some pieces of the software, may still refer to this older name.
Certbot website at EFF.org (the Electronic Frontier Foundation).
Automation[edit | edit source]
Ansible has a ACME certificate module in the crypto' collection (community not core). However, using it is a two-step process. We opted instead to create an integration into the Meza platform that takes care of both installation and renewal.
With HAProxy[edit | edit source]
Like Lighttpd, Pound, Ejabberd and other servers, HAProxy expects a single .pem file that has the combined contents of the fullchain.pem and privkey.pem.
Fortunately, certbot offers a --pre-hook, a --post-hook and a --renew-hook that we can use. The hooks allow to stop and later restart the 'normal' services and also concatenate the generated certificate files into a .pem file for HAProxy.
Do not use the plugin.
On Amazon[edit | edit source]
If you're one of the millions of Amazon Web Services customers, you may be tempted to use their lookalike service called AWS Certificate Manager.
Don't.
AWS certificates can't even be copied between regions. AWS certificates can't be used on your own servers. AWS certificates have annoying limits. They use email in whois to validate (not going to work if you have domain privacy turned on)!!! Amazon should have just joined the rest of the world in supporting LetsEncrypt. Fortunately, LetsEncrypt can be used everywhere, including AWS.
On Cloudflare[edit | edit source]
Cloudflare offers "Keyless SSL" and "Universal SSL". Although these are excellent signs that Cloudflare is doing good work, it remains true that origin traffic may not be encrypted at all leading to a huge trust problem.[2]
The best way for Cloudflare customers to encrypt fully, is to use Certbot. Cloudflare support echoes word-for-word what Let's Encrypt says in their community forum: How to get a Let's Encrypt certificate while using CloudFlare
tldr; Use the --webroot-path option with the certonly --preferred-challenges="dns", but you'll need to manually intervene. Optionally, if you just turn off the proxying while you issue the certificate, you can use TLS-SNI and HTTP-01 challenges (and then turn proxying back on.) For more advanced usage, check out the docs where they describe pre and post validation hooks
With the pre-hook and post-hook options, you can script the conditions needed to authenticate and renew.
certbot renew --pre-hook "service nginx stop" --post-hook "service nginx start"
The --renew-hook only runs when a certificate has been successfully renewed, so use this script to do things like concatenate the fullchain and
Resources[edit | edit source]
- https://letsencrypt.org/getinvolved/ Get Involved with Lets Encrypt
- https://letsencrypt.org/getting-started/ Getting Started
- https://github.com/letsencrypt/letsencrypt Code on GitHub
- https://letsencrypt.readthedocs.org/en/latest/ Docs
- Apache docs
- Ubuntu Server Guide - Certificates and Security
- Ansible role for LetsEncrypt
FAQ[edit | edit source]
- How do I obtain a new certificate?
- setup the SSL virtual host in Apache, and be sure to include some
SSLCertificateFileandSSLCertificateKeyFiledirectives using the "snake-oil" certs.
e.g.
SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem
SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key - Then run certbot
/opt/certbot/certbot --apache -d example.org,www.example.org,wiki.example.org --dry-run
/opt/certbot/certbot --apache -d example.org,www.example.org,wiki.example.org
- setup the SSL virtual host in Apache, and be sure to include some
- What certs do I have?
- sudo certbot certificates
- How do I see more info about my certificates?
- You can view the 'Security' pane in Chrome Developer Tools, but for quicker access from the command-line, use openssl
sudo openssl x509 -in /etc/haproxy/certs/demo.qualitybox.us.pem -text
- Using
keytoolyou can also quickly inspect the certificate of a host: sudo keytool -printcert -sslserver equality-tech.com
- How do I expand a cert to include some sub-domains?
- Use the
--expandoption to put multiple domains in the same cert. - sudo /opt/certbot/certbot certonly --cert-name example.org --expand -d example.org,www.example.org,wiki.example.org,example.com,www.example.com,wiki.example.com
- How do I create a wildcard certificate with LetsEncrypt?
- See https://github.com/geerlingguy/ansible-role-certbot/pull/60#issuecomment-423919284
- How do I cleanup my old/test certificates?
- sudo /opt/certbot/certbot revoke --cert-path /etc/letsencrypt/live/baz.example.org/cert.pem
- sudo /opt/certbot/certbot delete --cert-name baz.example.org